Diagram A Secure Network Design For An Enterprise Network Lo
Network security diagrams Network security architecture diagram Computer networks diagrams encryption controls premise conceptdraw explain protect overview communications configuration policies
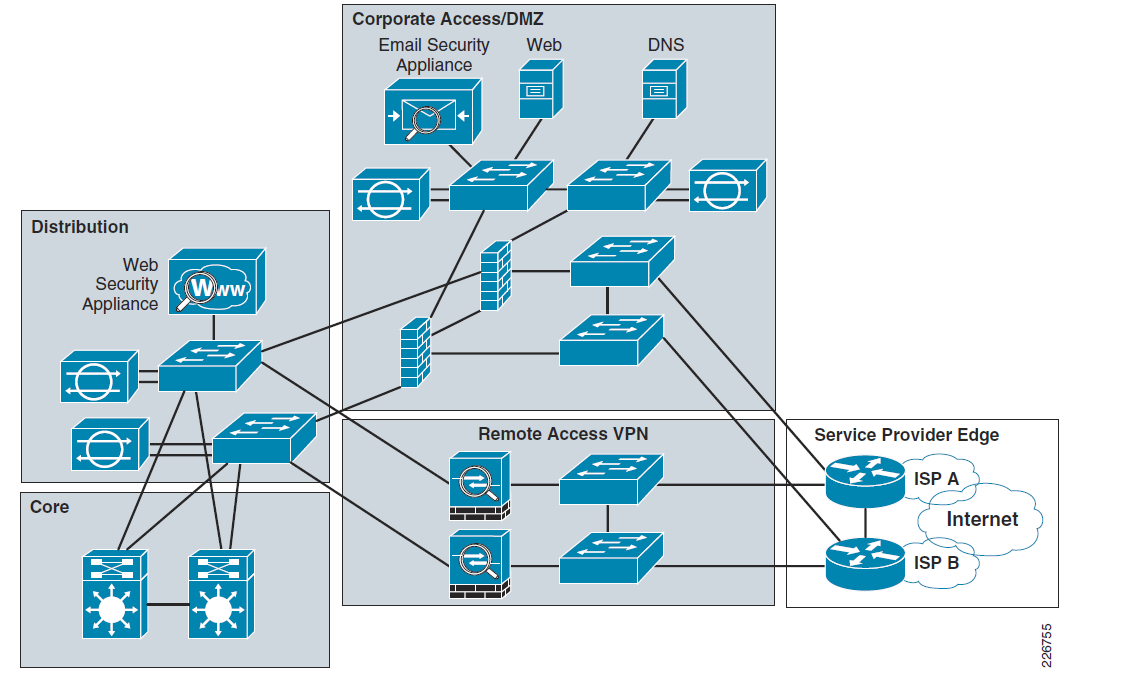
[PDF] Design and Implementation of a Network Security Model for
Network diagram computer drawing architecture circuit examples example diagrams smartdraw infrastructure networking software business small secure make templates wiring choose Recommended design for a secure network architecture A network topology is the arrangement of a network, including its nodes
Magic transit makes your network smarter, better, stronger, and cheaper
20+ low level diagram networkSecurity network diagram control computer devices diagrams access networks cloud model solution encryption secure examples premise architecture conceptdraw example software Enterprise edge internet cisco ccda moore trek shawn designingImplementation firewall router cooperative.
Logical network diagramNetwork security diagram Network security diagram wireless computer firewall wan example diagrams secure lan architecture networks clipart between drawing devices conceptdraw networking systemCisco topology networking nodes arrangement creately administrator connecting.

Shawn moore's it trek: enterprise internet edge design
Network security diagrams[diagram] home lan diagram Network diagram security lucidchart examples template topology templates lan wan firewall area transit magic local chart networking gif management wideHow to design a secure network infrastructure.
Computer network architecture tutorial and exampleOverview of on-premise and cloud network security controls – thecloudxperts Infrastructure 18thNetwork diagram architecture.

[pdf] design and implementation of a network security model for
.
.





![[PDF] Design and Implementation of a Network Security Model for](https://i2.wp.com/d3i71xaburhd42.cloudfront.net/a4a5ef4f2e937dc407a4089019316b054e8e3043/10-Figure1-1.png)


